
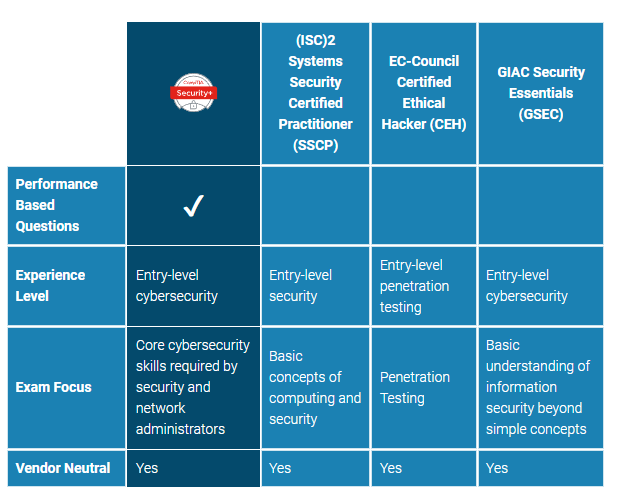
CompTIA Security+ is a global certification that validates the baseline skills necessary to perform core security functions and pursue an IT security career.
baseline cybersecurity skills are applicable across more of today’s job roles to secure systems, software and hardware.
chosen by more corporations and defense organizations than any other certification on the market to validate baseline security skills and for fulfilling the DoD 8570 compliance.
the only baseline cybersecurity certification emphasizing hands-on practical skills, ensuring the security professional is better prepared to problem solve a wider variety of today’s complex issues.
covering the most core technical skills in risk assessment and management, incident response, forensics, enterprise networks, hybrid/cloud operations, and security controls, ensuring high-performance on the job.
Globally recognized certification that validates the foundational knowledge and skills required to perform core security functions and pursue an IT security career. It covers a broad range of topics, including network security, cryptography, identity and access management, threats and vulnerabilities, risk management, and security operations and incident response.
Everyone
30+ hours
Online Bootcamp
english and tamil
Focusing on more threats, attacks, and vulnerabilities on the Internet from newer custom devices that must be mitigated, such as IoT and embedded devices, newer DDoS attacks, and social engineering attacks based on current events.
Includes coverage of enterprise environments and reliance on the cloud, which is growing quickly as organizations transition to hybrid networks.
Expanded to focus on administering identity, access management, PKI, basic cryptography, wireless, and end-to-end security.

Covering organizational security assessment and incident response procedures, such as basic threat detection, risk mitigation techniques, security controls, and basic digital forensics.
Expanded to support organizational risk management and compliance to regulations, such as PCI-DSS, SOX, HIPAA, GDPR, FISMA, NIST, and CCPA.
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Topic 2A: Explain Threat Actor Types and Attack Vectors.
Topic 2B: Explain Threat Intelligence Sources.
Topic 3A: Assess Organizational Security with Network
Reconnaissance Tools.
Topic 3B: Explain Security Concerns with General Vulnerability Types.
Topic 3C: Summarize Vulnerability Scanning Techniques.
Topic 3D: Explain Penetration Testing Concepts.
Topic 4A: Compare and Contrast Social Engineering Techniques.
Topic 4B: Analyze Indicators of Malware-Based Attacks .
Topic 5A: Compare and Contrast Cryptographic Ciphers.
Topic 5B: Summarize Cryptographic Modes of Operation.
Topic 5C: Summarize Cryptographic Use Cases and Weaknesses.
Topic 5D: Summarize Other Cryptographic Technologies
Topic 5A: Compare and Contrast Cryptographic Ciphers.
Topic 5B: Summarize Cryptographic Modes of Operation.
Topic 5C: Summarize Cryptographic Use Cases and Weaknesses.
Topic 5D: Summarize Other Cryptographic Technologies
Topic 6A: Implement Certificates and Certificate Authorities.
Topic 6B: Implement PKI Management.
Topic 7A: Summarize Authentication Design Concepts.
Topic 7B: Implement Knowledge-Based Authentication.
Topic 7C: Implement Authentication Technologies.
Topic 7D: Summarize Biometrics Authentication Concepts
Topic 8A: Implement Identity and Account Types.
Topic 8B: Implement Account Policies.
Topic 8C: Implement Authorization Solutions.
Topic 8D: Explain the Importance of Personnel Policies.
Topic 9A: Implement Secure Network Designs.
Topic 9B: Implement Secure Switching and Routing .
Topic 9C: Implement Secure Wireless Infrastructure.
Topic 9D: Implement Load Balancers .
Topic 10A: Implement Firewalls and Proxy Servers.
Topic 10B: Implement Network Security Monitoring.
Topic 10C: Summarize the Use of SIEM..
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Topic 11A: Implement Secure Network Operations Protocols.
Topic 11B: Implement Secure Application Protocols.
Topic 11C: Implement Secure Remote Access Protocols.
Topic 12A: Implement Secure Firmware.
Topic 12B: Implement Endpoint Security.
Topic 12C: Explain Embedded System Security Implications.
Topic 13A: Implement Mobile Device Management.
Topic 13B: Implement Secure Mobile Device Connections.
Topic 14A: Analyze Indicators of Application Attacks.
Topic 14B: Analyze Indicators of Web Application Attacks.
Topic 14C: Summarize Secure Coding Practices.
Topic 14D: Implement Secure Script Environments.
Topic 14E: Summarize Deployment and Automation Concepts
Topic 15A: Summarize Secure Cloud and Virtualization Services.
Topic 15B: Apply Cloud Security Solutions.
Topic 15C: Summarize Infrastructure as Code Concepts.
Topic 16A: Explain Privacy and Data Sensitivity Concepts.
Topic 16B: Explain Privacy and Data Protection Controls.
Topic 17A: Summarize Incident Response Procedures.
Topic 17B: Utilize Appropriate Data Sources for Incident Response.
Topic 17C: Apply Mitigation Controls..
Topic 18A: Explain Key Aspects of Digital Forensics Documentation.
Topic 18B: Explain Key Aspects of Digital Forensics Evidence Acquisition.
Topic 19A: Explain Risk Management Processes and Concepts.
Topic 19B: Explain Business Impact Analysis Concepts.
Topic 20A: Implement Redundancy Strategies.
Topic 20B: Implement Backup Strategies.
Topic 20C: Implement Cybersecurity Resiliency Strategies.
Topic 21A: Explain the Importance of Physical Site Security Controls.
Topic 21B: Explain the Importance of Physical Host Security Controls.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Senior Engineer in ABC Company
System Engineer in X Company
AI Engineer in D Company






Launch Date
Launch Date
Launch Date
SY0-601
SY0-601
Cybersecurity attacks continue to grow. Increasingly, more job roles are tasked with baseline security readiness and response to address today’s threats. Updates to Security+ reflect skills relevant to these job roles and prepare candidates to be more proactive in preventing the next attack. To combat these emerging threats, IT Pros must be able to:
• Help identify attacks and vulnerabilities to mitigate them before they infiltrate IS
• Understand secure virtualization, secure application deployment, and automation concepts
• Identify and implement the best protocols and encryption
• Understand the importance of compliance
Keep your certification up to date with CompTIA’s Continuing Education (CE) program. It’s designed to be a continued validation of your expertise and a tool to expand your skillset. It’s also the ace up your sleeve when you’re ready to take the next step in your career.
Get the most out of your certification
Information technology is an incredibly dynamic field, creating new opportunities and challenges every day. Participating in our Continuing Education program will enable you to stay current with new and evolving technologies and remain a sought-after IT and security expert.
The CompTIA Continuing Education program
Your CompTIA Security+ certification is good for three years from the day of your exam. The CE program allows you to extend your certification in three-year intervals through activities and training that relate to the content of your certification. Like Security+ itself, CompTIA Security+ ce also carries globally-recognized ISO/ANSI accreditation status.
It’s easy to renew
You can participate in a number of activities and training programs, including higher certifications, to renew your CompTIA Security+ certification. Complete CertMaster CE, an online, self-paced CE course, or collect at least 50 Continuing Education Units (CEUs) in three years, upload them to your certification account, and Security+ will automatically renew.
Want more details? Learn more about the CompTIA Continuing Education program.
CompTIA Security+ Exam Voucher
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.


Copyright HebeSec Technologies Pvt. Ltd. © 2023. All rights reserved
